Introduction
This chapter discusses the role of Joint Intelligence, Surveillance, and Reconnaissance (JISR) in support of countering Unmanned Aircraft Systems (UAS) and the essential contributions of the different intelligence collection disciplines throughout all phases of the C-UAS methodology described in the previous Chapter. This chapter will also highlight how JISR can support UAS related threat assessments at all levels and it provides an outlook of potential future challenges regarding JISR.
The proposed C-UAS Methodology (cf. Figure 5.1, p. 76) comprises a broad range, from deterrence to neutralization, and from preventive to reactive countermeasures. A prerequisite to successfully apply this method are defined threat vectors. Although these vectors are not always predictable with absolute certainty, JISR can provide probabilities if a threat exists and how it could evolve, so C-UAS measures can be planned and developed accordingly. Because of this, the intelligence cycle and the JISR process have to start even before the described C-UAS Methodology comes into play. Then, once a threat is identified, JISR also needs to continuously accompany and support every single line of effort within the C-UAS Methodology.
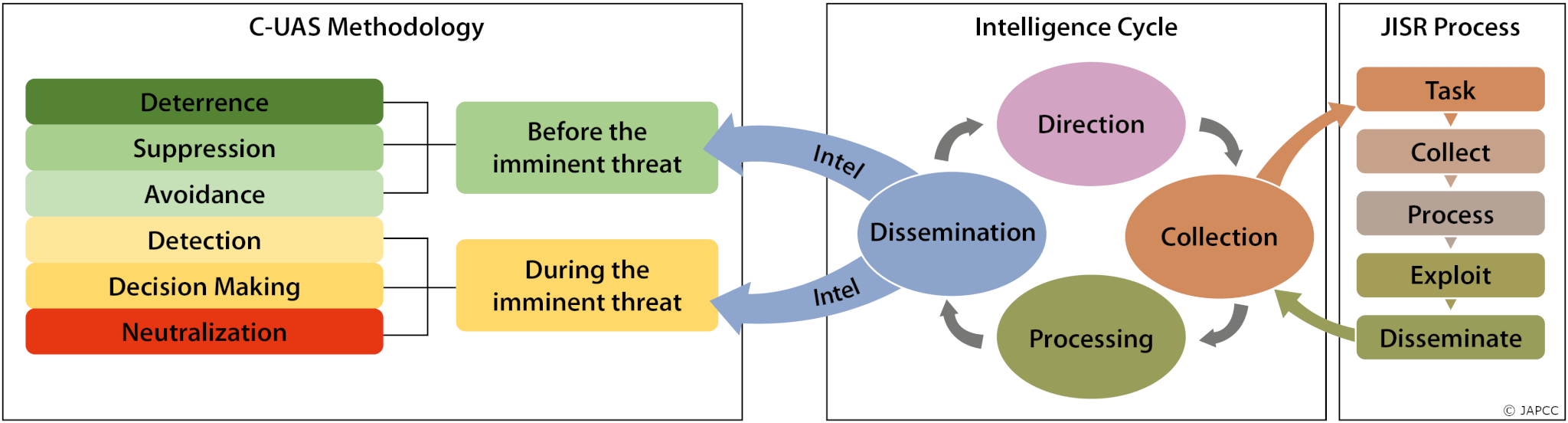
Taking Preventive Action: The Joint Intelligence Preparation of the Operational Environment
According to Frank Herbert’s famous quote, taking preventive action against a threat requires knowledge of its existence. Hence, the first step to prepare for countering UAS is to identify how likely a threat is to occur, how it is likely to emerge, and from where it might originate.
‘The first step in avoiding a trap is knowing of its existence.’
Frank Herbert, from his 1965 novel ‘Dune’
By definition1 a threat can be described as ‘an expression of intention to inflict evil, injury, or damage’. However, this definition covers only the intent of potential adversaries willing to impose a threat, but not the means to do so. To constitute a valid threat, both factors need to be accounted for. Therefore, JISR has to identify the potential adversaries and their intent, as well as their available means to pursue their objectives. Chapter 3 (cf. p. 34 ff.) describes some potential threat scenarios originating from various actors, ranging from consumer and commercial drones operated by individuals to advanced UAS employed by state-sponsored organizations or regular armed forces. Although the actual countermeasures against these threats may differ, the intelligence requirements and JISR contributions to the C-UAS process as a whole will remain unchanged.
‘[…] the establishment of a common threat database […] will enhance identification and classification and will help reduce fratricide. In the case of UAS, everything is enemy – until proven friendly. […] Establishing a common UAS database, with a single intelligence organization responsible for its operation, would provide a considerable advantage for the warfighter’.2
Colonel Matthew T. Tedesco, United States Army
With regard to C-UAS, intelligence collection and analysis should be focused on a potential adversary’s unmanned systems inventory, these systems’ capabilities and anticipated performance, as well as their possible evolution in the future.3 Therefore, UAS require consideration and implementation in both the intelligence cycle and the JISR process. To develop an effective C-UAS standard, all intelligence activities should take the following information requirements about a potential adversary’s drones and UAS into account:4
- General System Features and Characteristics;
- Physical Structure of the UAS;
- Sensors and Weapons Capabilities;
- Possible System Adaptations;
- System Interoperability, especially Sensor-Shooter Interrelations;
- Command & Control, especially Radio Frequencies;
- System Vulnerabilities, Resilience and Redundancy;
- Logistic Supply Chain and Contractors;
- Tactics, Technics and Procedures (TTP);
- Potential Chemical, Biological, Radiological, and Nuclear (CBRN) upgrades.
Following collection, the above data needs to be processed and assessed as to whether and how a threat can be deterred, suppressed or avoided. This assessment is provided by the intelligence cycle which is supported by the JISR process. A plain technical analysis of an unmanned system and the deduction of its potential capabilities can already provide a reasonable estimate of its ability to impose a threat on friendly forces. However, as already mentioned, the potential adversary, their intent, and their willingness to inflict harm need to be taken into the equation as well. To do so, there are two possible approaches, depending on how much time and analytical resources are available:
Identify possible actors which pose a threat and then analyze their UAS capabilities. This approach focuses on the potential adversary and has the advantage of significantly reducing the number of UAS to be assessed. Facing clear signs of an emerging crisis or a likely adversary, it is a very efficient way to analyze the threat, especially when time is a critical factor.
Identify all UAS which could pose a threat and then merge these with possible hostile actors if required. Establishing a common threat database of most UAS requires significant time and effort but has the advantage of having knowledge readily available when required. This, in turn, would be significantly beneficial for the first approach, when time is critical.
Both approaches have their own relevance and should complement each other to successfully contribute to the Joint Intelligence Preparation of the Operational Environment (JIPOE).5 The most relevant intelligence gathering disciplines that can contribute to both approaches and the JIPOE are briefly discussed in the following sections.
Open Source Intelligence (OSINT) can exploit, for example, catalogues and advertisements of different commercial UAS manufacturers, or analyze market trends at commercial and scientific exhibitions and conferences. Like with any other information, these sources must be thoroughly assessed with regard to their credibility and reliability as open-source information is generally vulnerable to falsification and should not be accepted as the main source of intelligence. Many governmental and non-governmental intelligence agencies use open sources to release fake or biased versions of news stories. Chapter 16 (cf. p. 283 ff.) discusses countering disinformation in more detail. Nevertheless, OSINT remains a good source of information to track emerging UAS technologies and the evolution of unmanned systems for civil, public, as well as military applications.
Imagery Intelligence (IMINT) can provide relevant information on an adversary’s UAS inventory, the numbers and types of systems, as well as their supporting equipment. Imagery of UAS components, for example satellite ground terminals and ground control stations or dedicated UAS ammunitions and spare parts near an airfield, if visible, can reveal the presence of a UAS capability without having to detect the actual unmanned aircraft. Frequent imagery of suspected or identified UAS locations can help reveal new acquisitions of systems and identify upgrades in UAS capabilities. For example, satellite terminals which were not present before, could indicate a new Beyond Line of Sight (BLOS) capability.
Technical Intelligence (TECHINT) concerns itself with foreign technological developments and the performance and operational capabilities of foreign materials, which have or may eventually have a practical application for military purposes.6 As UAS technology is a global phenomenon, TECHINT does not necessarily require captured enemy materiel. Technical analysis of common UAS components manufactured in neutral or friendly countries and distributed by a global supply chain (for instance EO/IR sensor chips, microprocessors or engine parts) could provide sufficient insight into a foreign unmanned system’s capability.
Human Intelligence (HUMINT). UAS activities always involve people, whether in research and development, production, or deployment. HUMINT can approach these human resources, either overtly or covertly, to gain more specific information than technical systems, like satellites, could provide. However, HUMINT is thoroughly based on the credibility and reliability of the human source targeted.
Acting on the Imminent Threat: the ‘S’ in JISR
Once a UA is airborne, surveillance as an integral part of JISR becomes relevant. In an operational environment, JISR responds to the Commander’s Critical Information Requirements (CCIR)7 by applying tactics, techniques and procedures to detect, identify, and disseminate intelligence data in support of C-UAS and the operational planning process.
Detecting UA in flight is often the first step in defending against them. Larger UA can be detected even with legacy radar systems, whereas Low, Slow and Small (LSS) drones require more specialized equipment to distinguish them from clutter, e.g. leaves and birds. However, apart from airspace surveillance, reliable identification of the intruding UAS and its capabilities, as well as identifying the origin of the C2 transmission, is critical for selecting appropriate countermeasures. To provide this reliable identification as a pre-condition for high confidence real-time decisions, including weapons engagement, all intelligence collecting disciplines have to contribute the necessary data. For example, this includes information about the capabilities and the level of autonomy of the UAS, locations of adversary Launch & Recovery Elements (LRE) and Mission Control Elements (MCE), as well as SATCOM assets and the frequencies used. C-UAS systems must be fed with this information, preferably in real-time, to process a suitable target solution. The most relevant intelligence gathering disciplines that can contribute to surveillance are briefly discussed in the following section.
Acoustic Intelligence (ACINT) collects and exploits acoustic signals or emissions.8 ACINT has some long-established applications in the maritime environment (sonar) but is also used to locate rocket launch sites or artillery firing positions. Dedicated acoustic detection systems for locating UAS in flight are already developed and available on the market, but their current effective range is limited to less than a few kilometres. At longer distances, the environmental noise will simply mask the sound emissions from the UAS’ engine and propeller. Chapter 4 (cf. p. 58 f.) discusses drone and UAS audibility in more detail. However, ACINT systems could be relevant at the tactical level and a built-in database of acoustic drone signatures could support the identification of the detected drone model and manufacturer.9
Imagery Intelligence. The vast majority of surveillance is conducted in the optical spectrum, to include not only visible but also infrared and ultraviolet light emissions. IMINT can identify the infrastructure and support equipment necessary to operate larger UAS not only during the JIPOE, as already discussed, but also during the Battle Damage Assessment (BDA) process once these targets have been engaged. Moreover, IMINT can actively pursue the identification of temporary UAS launch sites and mobile launch platforms. On the tactical level, dedicated C-UAS systems are typically equipped with an additional EO/IR camera to augment the primary sensor and to support the operator in validating the detected object.
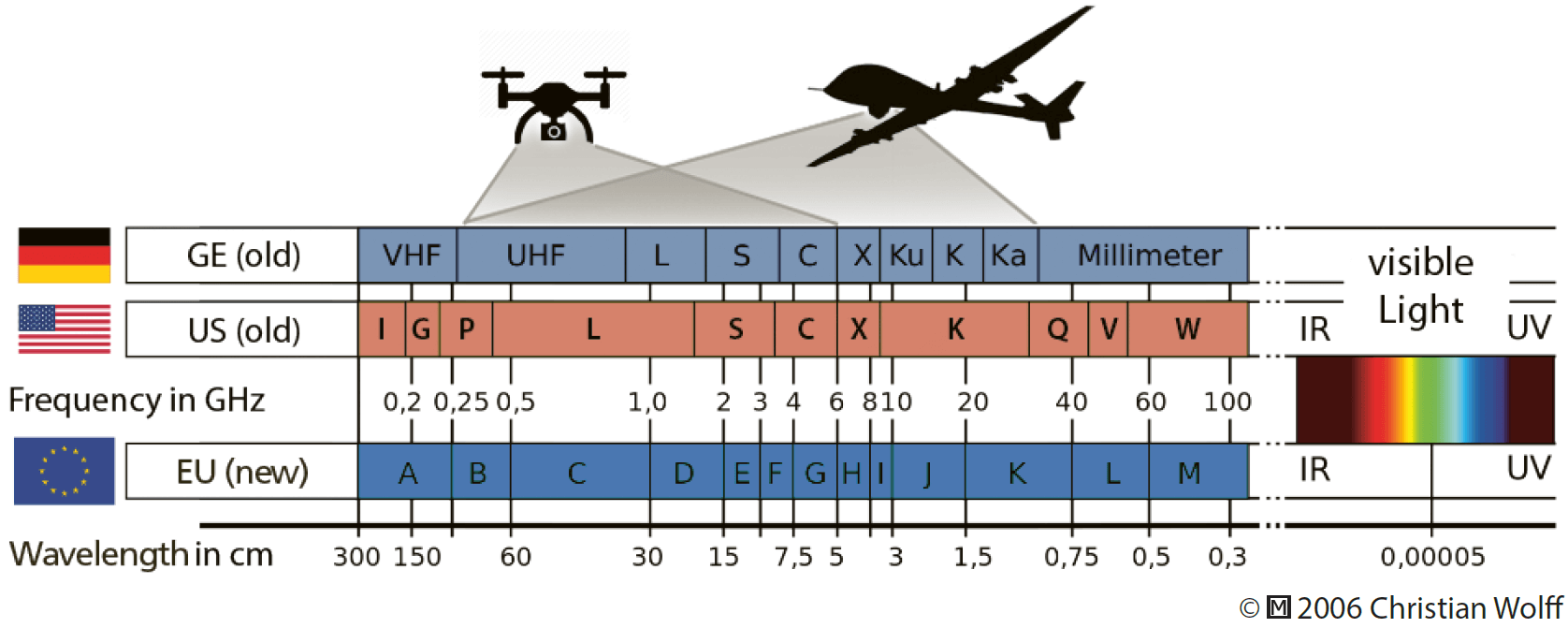
Signals Intelligence (SIGINT) collects and exploits transmissions throughout the entire radio frequency spectrum. If not fully autonomous, almost any UAS relies on electronic communications and one or more data links. Figure 6.2 depicts the frequencies used by the majority of current drone and UAS models. SIGINT can detect and intercept UAS transmissions and analyze the respective signal to identify the drone or UAS. The exploitation of the transmitted data may reveal significant information about the UAS, like its location, planned flight route, engine status, and more. Similar to the recommended audio database for ACINT, it is desirable to implement a comparable approach in the SIGINT domain, to include: UAS data link frequencies, waveforms, protocols, and encryption methods.
Other intelligence disciplines, such as Measurement and Signature Intelligence (MASINT) or Scientific and Technical Intelligence (STI)10 are required to support this SIGINT approach because they provide the relevant information about the respective UAS and the technical analysis of their radio frequencies.
Human Intelligence. Although HUMINT could not directly contribute to surveillance and countering an imminent UAS threat, it can fill data collection gaps and provide additional intelligence about: locations of temporary launch sites and UAS ground elements, logistic support routes, or regular launch & recovery schedules. Interrogation of captured personnel could provide more reliable information on enemy UAS and their capabilities.
General Reporting Procedures. JISR depends on a continuous flow of information, which does not necessarily only need to originate from the specific intelligence disciplines. The eyes and ears of every soldier are highly valuable sensors to augment the data collection and could help to complete the situational picture. Chapter 15 discusses reporting procedures and the respective requirements for education and training in more detail.
Tasking, Collection, Processing, Exploitation and Dissemination
Drones and UAS require consideration throughout the entire Tasking, Collection, Processing, Exploitation and Dissemination (TCPED)11 process to raise awareness on this new type of threat and as a prerequisite for any defensive measures to follow. This is likely to require contributions from all of the aforementioned intelligence collection disciplines and their associated sensors. TCPED needs to develop applications and tools to store drone- and UAS-related technical data and signatures to enable intelligence and C-UAS systems to utilize that information for the identification of the respective drones and UAS. Establishing a common UAS database will likely accelerate the TCPED process with regard to UAS identification and enable more flexible support to ad hoc and dynamic requests. Notably, the sooner information about drones and UAS is collected and analyzed, the more effectively the recommended database could be utilized. Therefore, all intelligence disciplines need to consider pre-emptive data collection of potential adversaries’ UAS, but also of dual-use consumer and commercial drones.
Three Considerations for Adapting to the C-UAS Challenge
According to NATO AJP-2.7 ‘the harmonization of intelligence and operations functions is essential to maximize the efficiency and effectiveness of the employment of JISR capabilities’.12 In the C-UAS context, three considerations about the key elements of JISR and its associated processes should be made, namely about agility, adaptability and innovation.
Agility
The purpose of intelligence is to gather, analyze and disseminate information to support the decision-making cycle at all levels of operations. Drones and UAS represent a complex challenge as there is a multitude of different models with different characteristics and capabilities. Larger systems can consist of many different components which are dispersed throughout all domains, to include air, land, space, and even cyberspace. Collecting information about all the different drones and UAS as well as their components and characteristics in all of these domains is likely to result in an ‘ocean’ of stored data and information. Consequently, the JISR architecture requires a high level of agility in managing this vast amount of information. This agility may only be achieved with the help of automated processes and probably computer-aided analytics and decision-making support.
Adaptability
The recent decades have seen a significant change and evolution of warfare. It shifted from global war against terrorism to a near-to-peer or peer-to-peer confrontation. Nuclear, biological and chemical weapons have been uncontrollably spread to states that should never have been allowed to get their hands on these technologies. In the same way, the ever-accelerating development and proliferation of drones and UAS are enabling potential adversaries to acquire new, previously non-existent capabilities. Hence, JISR needs to adapt to these emerging capabilities and enhance the awareness of the C-UAS challenge. Adaptability might also be required when urgent Collection Requirements (CRs) emerge, and the analysis of adversary UAS receives a high priority in operational planning. NATO doctrine already states that its JISR architecture should be adaptive to ‘rapid reconfiguration’.13 With respect to drones and UAS, this implies the consideration of the different domains in which the individual components of the UAS operate and the geographical region from which they are controlled. It also requires consideration of enemy UAS inventories, including dual-use commercial systems, as well as enemy UAS and drone tactics, techniques, and procedures, to create a comprehensive awareness of how to counter the UAS threat. To highlight the importance of adaptability, Chapter 3 (cf. p. 43 f.) provides an example of how Russian forces directed and adjusted fires in Eastern Ukraine with simple commercial off-the-shelf drones.
Innovation
Innovative technologies and methods offer many opportunities for data collection, processing, and exploitation. JISR should not be limited to classically exploiting information, but rather should initiate an innovative way of thinking how to incorporate the various drone and UAS components into the Collection Task List (CTL). In a complex environment, the use of cognitive analysis tools for the exploitation of high-resolution images and the automatic identification of moving objects are just two examples of potential ways to implement computer-aided analysis support. This may help to reduce the workload of limited, valuable human resources. Eventually, data analytics techniques may be able to automatically generate JISR results,14 and significantly reduce the required time to deliver reliable information about potential UAS threats.
Conclusion
Drones and UAS are complex systems which do not only consist of the unmanned aircraft. All of the different system components may provide individual opportunities for countermeasures and need discreet consideration in the JIPOE. JISR has to provide the relevant data of enemy UAS and their components. This large amount of information needs to be stored in advance, preferably in a common database, so that it can be made available at the beginning of any operational planning. This database would also help to
feed timely, actionable intelligence into the targeting cycle to support the C-UAS weapon systems embedded in the proposed C-UAS methodology. This may require the design of a more modern and connected intelligence structure and information sharing policy amongst the NATO member states. In this context, it is important that the interfaces between JISR, the intelligence cycle, and the targeting cycle are well defined, synchronized and harmonized. Personnel from the aforementioned disciplines have to be trained in the collaboration between these processes. To further improve cooperation, it is advisable to deepen this during exercises in order to get a routine and common understanding of the processes.