Background
In recent decades, Unmanned Aircraft Systems (UAS) have been fielded in every military service, ranging from handheld micro-UAS to medium-sized tactical systems to full-grown Remotely Piloted Aircraft (RPA). At the same time, the civilian market has witnessed an exponential growth of predominantly smaller systems intended for public and recreational use. However, the latter use case has gained the attention of law enforcement agencies and military force protection communities due to the increased misuse of Commercial-Off-The-Shelf (COTS) ‘drones’ in the vicinity of airports, public events and military installations.
Recently, various industries reacted to the emerging demand for capabilities to defend against these COTS UAS by developing Counter-UAS (C-UAS) sensors and effectors. These systems are specifically designed to detect, track, and engage Low, Slow and Small (LSS) flying objects, ranging from man-portable systems such as ‘Droneguns’1, 2, 3 to truck-mounted models such as the ‘Silent Archer’.4 NATO also reacted to this new threat by conducting a series of studies centered on defence against LSS air threats5-11 and by establishing a C-UAS Working Group with a focus on terrorist misuse of UAS.12
However, technology is developing rapidly, in many cases, faster than the defence industry or NATO can react. For example, many ‘traditional’ countermeasures against small UAS rely on electronic jamming of the Command and Control (C2) link between the ‘drone’ and its remote control. Many current COTS products are, however, able to navigate autonomously to a given coordinate or can be controlled via a Global System for Mobile Communications (GSM) network from the operator’s mobile phone. These features make jamming either completely useless, since the C2 link is no longer required to navigate, or unavailable, because of peacetime restrictions that prohibit the jamming of frequencies that are in use by the public.
Additionally, a sole focus on the LSS end of the C-UAS spectrum covers only a fraction of current UAS technology and excludes most military applications. Peer competitors to NATO can be expected to employ UAS at the same level of technology, and under comparable operational principles, as the Alliance. Consequently, NATO has to anticipate enemy use of UAS in the same mission sets as friendly UAS, covering the spectrum from Intelligence, Surveillance & Reconnaissance (ISR) to unmanned airstrikes, conducted in Line of Sight (LOS) as well as Beyond Line of Sight (BLOS) operations, utilizing the electromagnetic spectrum and the space domain in the same way as NATO.
The following sections briefly describe a spectrum of C-UAS considerations and why the current focus on the LSS end, although imminent and essential, is not sufficient to cover all aspects of defence against potential adversary UAS engagements.
The Spectrum of Countering Unmanned Aircraft Systems
To understand the full spectrum of countering UAS, it is important to note that exclusively focussing on the Unmanned Aircraft (UA) or ‘drone’ does not provide the complete picture. UAS are grouped into several categories and consist of numerous components, depending on their size and application.
Unmanned Aircraft System Components
The basic setup of a small UAS consists of an operator, a remote control, a C2 link and the aircraft or ‘drone’ itself. Larger systems may also incorporate a dedicated Ground Control Station (GCS) for Launch and Recovery as well as a Mission Control Element (MCE) for conducting the operation. The larger systems typically utilize space-enabled BLOS communications for the C2 and data links. GCSs and MCEs consist of physical infrastructure such as trucks and containers or buildings, which typically host the computer hardware and software that, in turn, run the applications required to operate the overall system.
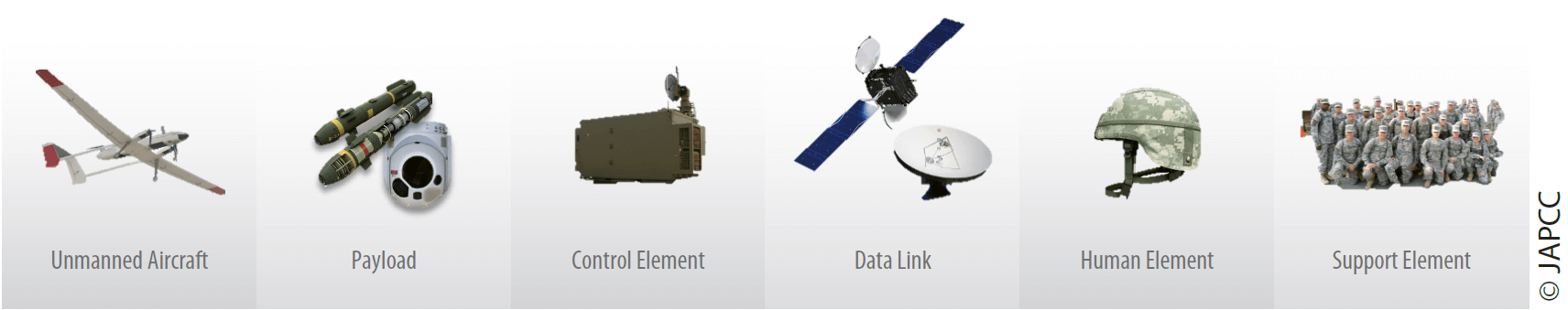
As a general rule, the larger the UAS, the larger the requirement for infrastructure such as shelters, runways, airfields or airports. The same is true for the amount of logistics support, such as fuel, ammunition, and maintenance.
Finally, unmanned systems always require personnel to operate them. This can vary from a single individual operating a small ‘drone’ up to multiple aircrew rotating in shifts in case of larger systems. Higher class military UAS performing collection missions also require a significant amount of Processing, Exploitation and Dissemination (PED) personnel to analyze the information provided by the UAS.
Unmanned Aircraft System Categories
NATO categorizes UAS into three dedicated classes, ranging from Class I for the micro, mini and small ones, to Class II for medium-sized, tactical systems, to Class III for Medium-Altitude Long-Endurance (MALE) and High-Altitude Long-Endurance (HALE) aircraft.13 By comparing the three different classes, their application, size and operating altitude alone, it can be concluded that countering this spectrum of UAS requires a multitude of different, class-specific approaches.
Unmanned Aircraft System Design Principles
Apart from their different classifications as described above, UAS also follow various design principles, according to their application and purpose. Depending on the specific UAS design features, detection and potential countermeasures may be challenged, denied or even not applicable.
Unmanned Aircraft. UA can be fixed-wing, rotary-wing, and some even incorporate stealth designs. Smaller systems (Class I) typically follow the rotary-wing principle, whereas larger systems (Class III) almost exclusively utilize a fixed-wing design. Tactical systems (Class II) follow both principles. Stealth designs are predominantly found with large HALE aircraft but sometimes also with tactical systems.
Propulsion. Throughout all classes, the majority of UA are propelled by a rotorcraft engine which allows for greater fuel efficiency and therefore longer endurance. However, some UA are equipped with jet engines, trading-in mission duration for faster speeds and larger payloads. Upcoming generations of UA are envisioned to incorporate hypersonic propulsion and may achieve airspeeds faster than Mach 5.
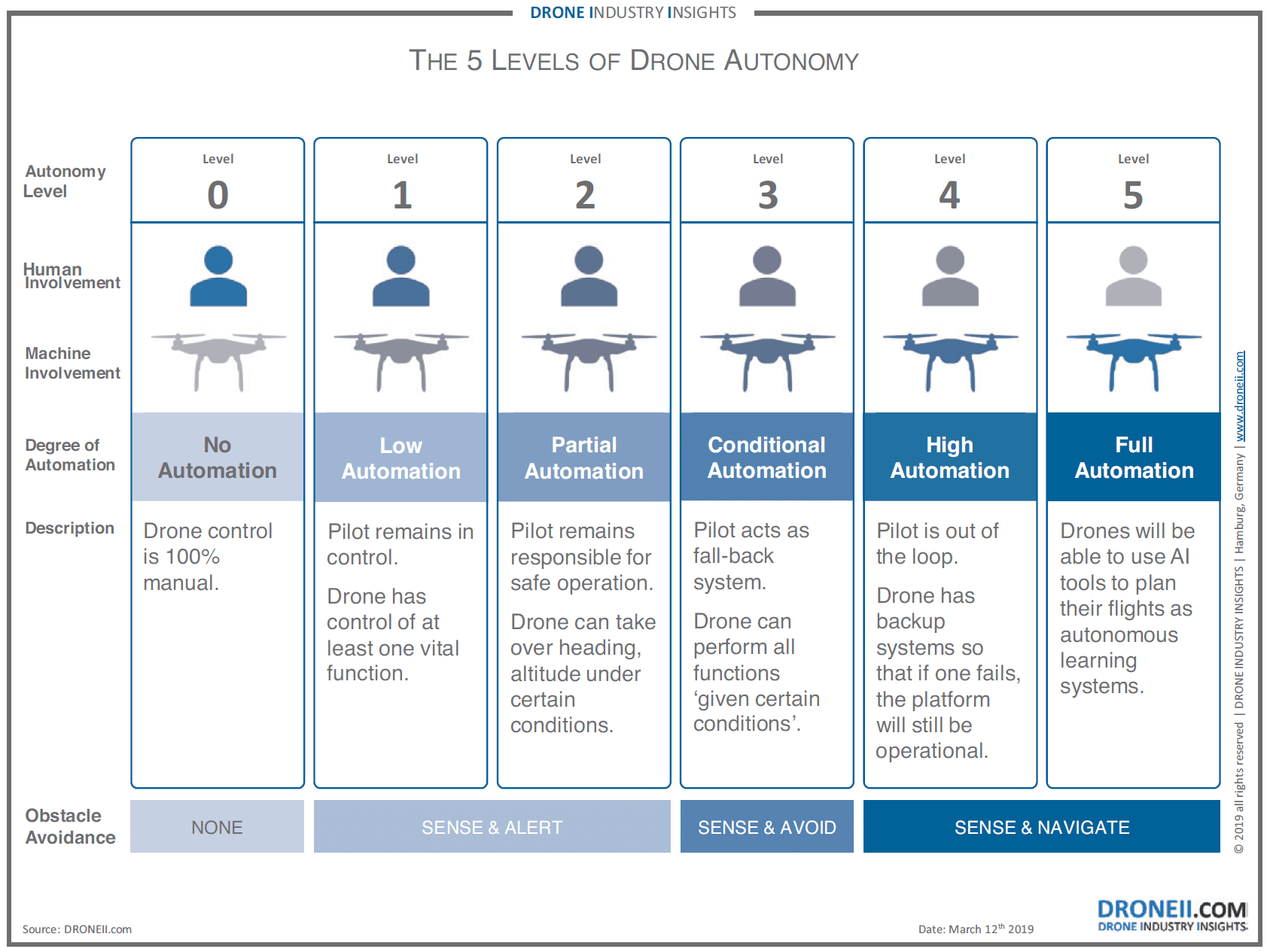
Communications. C2 of a UA is generally conducted via a LOS or BLOS radio link. Depending on the unmanned system’s level of autonomy (cf. Figure 1.2), this radio link is active either permanently or only on demand. UAS radio links encompass the range from common Wireless Networks up to dedicated satellite communications frequencies in the Ku-Band. The upcoming 5G standard will utilize even higher frequencies and mobile phone applications for command and control of UAS via GSM are already available on the commercial market. It is important to note that a potential adversary will most likely not utilize the same frequency bands as NATO and its partners.
Data Transmission. It can be anticipated that every radio link and every other form of digital communications between unmanned system components will be secured to a certain degree. Even commercially available ‘drones’ use either proprietary data link protocols or encryption to secure their communications.
A Comprehensive Approach to Countering Unmanned Aircraft Systems
Figure 1.3 provides an overview of UAS components and their relative spatial arrangements. Depending on the component itself, the domain it is operating in and its potential distance to NATO forces, there are different points of attack presented as options for the employment of countermeasures. While these points of attack can be addressed by the missions described in the sections below, all should complement each other and contribute to a comprehensive, multi-domain C-UAS effort.
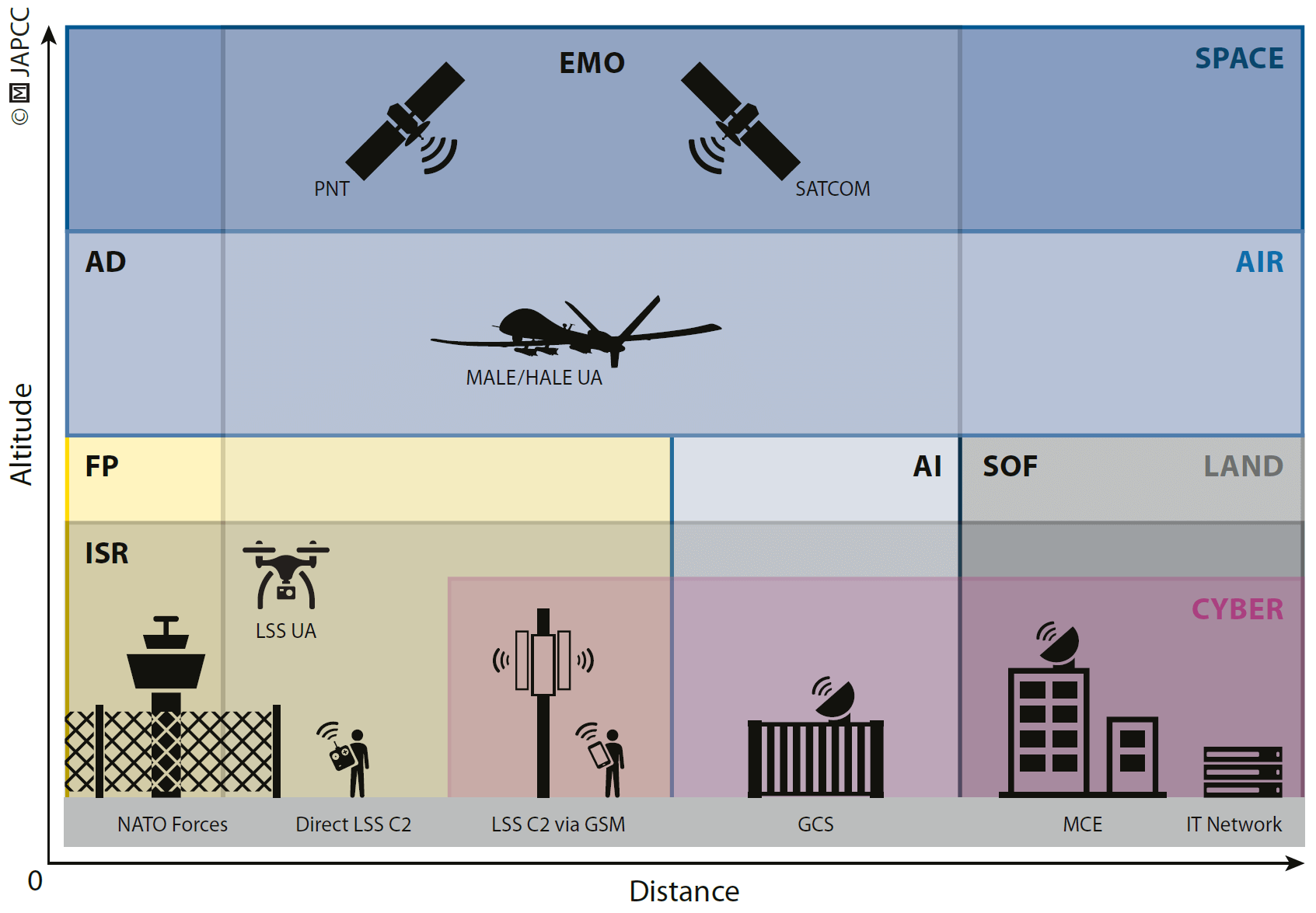
Force Protection
LSS UAS are readily available as COTS products to anyone and pose an imminent threat to critical public infrastructure and military installations. Force protection measures assuring the safety of friendly forces and critical infrastructure are typically focused on the area which requires protection. Natural and human-made obstacles such as trees or buildings can cover an approach of LSS UAS and significantly delay the detection of these objects in the area, further shortening available reaction time. Force protection measures should primarily be aimed at denying access of UAS to the protected area. However, it may also be desirable to safely capture the UAS for intelligence purposes.
Air Defence
Larger UAS can operate at altitudes of up to 30,000 ft., and in some cases even higher. The Radar Cross Section (RCS) of these UAS is comparable to any other legacy aircraft, hence can be detected and engaged by most Air and Missile Defence (AMD) systems. However, modern surface-to-air ammunition is not cheap and is designed to engage high-value targets. Large numbers or a swarm of low-cost UAS may quickly turn the cost-benefit ratio of traditional AMD upside down and render current systems inefficient. Short-Range Air Defence (SHORAD), Counter-Rocket, Artillery, and Mortar (C-RAM) systems, and even legacy Anti-Aircraft Artillery may provide an effective, but also efficient, defence against UAS.
Close Air Support and Air Interdiction
Launch and Recovery of larger UAS is typically conducted from a Ground Control Station (GCS) inside or near the mission area. GCS can be mobile and mounted on a truck, or stationary when placed on the ground, e.g. near an airfield. In any case, the Launch and Recovery Element (LRE) of larger UAS is a high-value target as it is often responsible for launching and recovering several UA. Eliminating an LRE will likely bring UAS operations to a halt in the respective area as new UAS cannot be launched anymore and airborne ones may not be recovered safely. Thus, AI may disrupt, degrade, deny or destroy an adversary’s unmanned capabilities before they can be even used against friendly forces.
Special Operations
Once airborne, larger systems can often be handed over from the LRE to an MCE and operated BLOS via Satellite Communications (SATCOM). The MCE can be located far outside the mission area, probably deep inside the adversary’s territory and utilizing a hardened infrastructure. NATO Special Operations Forces (SOF) may be employed as a means to attack the enemy’s MCE itself, take out the SATCOM ground nodes which are essential for UAS BLOS operations, or even kill adversary combatants such as UAS crew members during their time off duty.
Cyber Warfare
UAS are entirely dependent on their computer systems, information technology and network connectivity. Control stations, especially inside fixed installations such as an MCE, are potentially vulnerable to an attack through cyberspace, exploiting security vulnerabilities of their hardware and software but also by taking advantage of human failure, negligence or susceptibility. COTS UAS being operated via a GSM network are most likely only accessible through the cyberspace domain, since countermeasures in the electromagnetic spectrum may be off-limits, e.g. if frequencies are publicly used.
Electromagnetic Operations
C2 of UAS is conducted via LOS or BLOS radio transmissions and typically also reliant on Position, Navigation, and Timing (PNT) signals. Electromagnetic Operations (EMO) can be used throughout all tiers of UAS to hinder and disrupt C2 and PNT transmissions or even to spoof PNT information to divert or land the UAS. However, ‘traditional’ Electronic Warfare (EW) has its limits with modern models of UAS which are capable of autonomous flight and are no longer reliant on continuous data links. However, upcoming Directed Energy Weapons (DEW) such as High-Power Microwaves (HPM) or High Energy Lasers (HEL) may add kinetic capabilities to the EMO portfolio and could be used to render sensor payloads inoperable or destroy the UA itself.14
Intelligence, Surveillance, and Reconnaissance
Detecting UA in flight is often the first step in defending against them. Larger UA can be detected even with legacy radar systems, whereas LSS UA require more specialized equipment to distinguish them from clutter, e.g. leaves and birds. However, apart from airspace surveillance, reliable identification of the intruding UAS and its capabilities, as well as identifying the origin of the C2 transmission, is critical for selecting the appropriate countermeasures. This includes information about the capabilities and the level of autonomy of the UA, locations of adversary LREs and MCEs, as well as SATCOM assets and frequencies used. C-UAS systems have to be fed this information, preferably in real-time, to process a suitable targeting solution.
The Space Domain
SATCOM is an essential part of BLOS UAS operations. But COTS UAS also utilize PNT signals provided by respective satellite constellations. Within the limits of the ‘Outer Space Treaty’, countermeasures against space-based communications and PNT may be a legitimate option to defend against an entire fleet of adversary UAS. This does not necessarily require kinetic engagements by anti-satellite weapons. Indeed, ground or space-based jamming capabilities could be effective without risking the creation of large amounts of debris which could render entire orbits unusable for mankind.
Legal Considerations for the Enforcement of Countermeasures
Applications for UAS range from public and recreational purposes to military missions including airstrikes. Consequently, depending on their use, defending against these systems is governed by either domestic or international law, and the legal framework that needs to be applied is also dependent on whether it is peacetime or wartime.
Peacetime versus Wartime
Defending against UAS is not only a wartime requirement. Frequent incidents15, 16 have already proven that COTS ‘drones’ can easily be flown into restricted airspace and can stop an entire airport’s flight operations. It is only a question of time before the first incident will be witnessed over military installations, e.g. airbases, headquarters or military training grounds.
Depending on the country and its domestic laws, which are applicable during peacetime, circumstances may prohibit certain types of countermeasures and limit the options for defending against UAS. These possibly prohibited countermeasures include kinetic engagement of airborne UA, jamming of publicly used frequencies such as GSM or wireless networks, or interference with the commercial PNT signals.
In general, it can be assumed that countering UAS in peacetime will be subject to a multitude of civilian restrictions which may or may not fully apply in a conflict scenario. C-UAS doctrine and Tactics, Techniques and Procedures (TTP) need to include these particulars and adhere to individual legal environments.
Law Enforcement versus Military Engagement
In peacetime, the responsibility for the defence against ‘drones’ and UAS typically lies with civil law enforcement agencies. However, responsibilities may overlap near military installations and critical infrastructure. Moreover, law enforcement agencies may require military support since the equipment to detect, identify and engage UAS might reside only in the armed forces.
Hence, close cooperation and coordination between civilian law enforcement agencies and the armed forces are essential for a comprehensive C-UAS approach. Mutual exercises could help establish common C-UAS TTPs and ensure an effective level of interoperability between civil and military organizations.
Public Safety and Collateral Damage
The protection of civilians from harm is the primary principle of both international as well as domestic law. Therefore, defence against UAS requires consideration of the potential risks to human life, both in peacetime and in wartime. Civilians may be endangered by kinetic measures such as the shooting down of UA or an attack on its ground facilities.
Additionally, non-kinetic measures such as jamming radio frequencies or PNT signals may affect public and commercial communications infrastructure and therefore, may be restricted or completely off-limits. Especially in peacetime, countermeasures have to be balanced against potential adverse impacts on critical communication systems and possible economic losses.
Depending on the payload, e.g. biological toxins, chemical gases or explosives, it may be required to manoeuvre the UA out of range of friendly forces or civilians before the actual countermeasure can be employed. Therefore, ‘traditional’ C-UAS methods which take effect on the spot need to be reviewed, and new approaches such as capturing aerial vehicles and neutralizing payloads should be considered.
Pre-emptive versus Reactive Countermeasures
Larger UAS require a significant amount of computer hardware, software and networks to operate. Therefore, the cyberspace domain may offer potential countermeasures capable of rendering the entire network and communications infrastructure of one or more unmanned systems inoperable. However, countermeasures in the cyberspace domain may require more than only a defensive posture. Pre-emptive and disguised placement of ‘backdoors’ in adversary computer systems may ensure access to these networks when required and it is probably the only way to be prepared and react promptly to an imminent UAS threat.
Dedicated legislation may also assist in defending against UAS in such a way that COTS ‘drones’ are required to transmit an identification and positioning signal comparable to the regular civilian air and maritime traffic. Some manufacturers already equip their drones voluntarily with transponders that provide this information on a separate and unencrypted radio frequency. Of course, this will not prevent criminal or terroristic abuse of these systems, but if legislation was in place, any system not providing a transponder signal could be classified as potentially hostile.
Summary
This short introduction was intended to provide an overview of the complexity of having to counter UAS. Different classes, applications and design principles of the Unmanned Aircraft itself challenge or even deny certain types of countermeasures. Moreover, larger unmanned systems may include ground installations, data links, computer networks as well as logistics, support equipment and dozens of personnel. Hence, there is no ’one-size-fits-all’ solution to the C-UAS challenge.
Finally, countering UAS requires a comprehensive approach by all the military and also non-military disciplines who can project lethal and non-lethal effects on any of the components of an unmanned system. Additionally, all these potential countermeasures require review under the different legal frameworks applicable in wartime, but more importantly in peacetime. Typically, in peacetime, military and civil authorities usually own different powers which require close coordination when employing countermeasures.












