Introduction
Technology is transforming our lives every day. Although it provides many advantages, it can also be utilized to develop an effective or deadly weapon by potential adversaries. Among these technological advances are Unmanned Aircraft Systems (UAS) and the corresponding systems to defend against them. Both technologies, UAS as well as Counter-UAS (C-UAS) systems, are increasingly proliferated and potential adversaries develop or acquire these modern warfare technologies. The threat posed by UAS and C-UAS can be very high, hence the goal should be to counter their negative effects on friendly forces, preferably before these systems can unfold their full potential. In order to reduce the undesired effects of new threats on friendly forces, these threats may need to be addressed as new and highly sensitive targets within the scope of the Air Interdiction (AI) operations which are defined as a core counter-land mission to obstruct or destroy adversaries’ capabilities. With AI operations, basic components of UAS (such as UAS ground components, mission control elements, humans, airfields etc.) and C-UAS (especially some Air Defence systems used for C-UAS) can be disabled or rendered ineffective before battle. This chapter outlines how AI can support countering UAS in an early stage of their deployment by attacking their ground components, personnel, and logistics. This chapter also provides an excursion on how to challenge the enemy’s C-UAS systems and highlights some examples from recent Turkish warfighting experiences about how to enable operations of friendly UAS in an AI role.
Air Interdiction Fundamentals
By definition, AI is an air operation conducted to divert, disrupt, delay, degrade or destroy an adversary’s military potential before it can be brought to bear effectively. It is preventively directed against enemy targets that are not yet an immediate threat to hinder their later engagement against friendly forces. If total prevention is impossible, the enemy should at the very least arrive at the battle late, fatigued, with depleted logistics and low on ammunition and supporting systems.1
Physical destruction of the enemy surface force, supporting elements and supplies is the most direct of the aforementioned AI objectives. However, even the enemy’s perception of its imminent destruction can achieve substantial delay and diversion of resources, which can be as effective as physically destroying the target.2
It is crucial to concentrate the effects of counter-land operations against critical and sensitive targets, since AI assets are generally limited in numbers. AI targets should be determined based on importance, then prioritized based on operational campaign goals. To make the targeting decision sensible, air planners must have timely and accurate intelligence regarding the enemy’s capabilities. To accomplish effective AI, intelligence is a key consideration and indispensable to success. During target development, each targeting process must relate specific targets to objectives, desired effects, and accompanying actions. Interdiction should focus on those systems that will provide the greatest payoff and achieve the objective. Appropriate coordination of AI with other joint force components helps preserve friendly freedom of action.3 Hence, economy of force will be employed by expending minimum effort and forces for AI, and it paves the way for supporting efforts to allocate assets to other military objectives. Chapters 6 and 9 discuss the role of Joint Intelligence, Surveillance, and Reconnaissance (JISR) as well as the targeting process in more detail.
Air Interdiction Considerations for Adversary UAS Technologies
UAS and C-UAS technologies require consideration in the AI target development process, given the undeniable contributions they have already made on the battlefield. UAS are playing vital roles in battlefield operations and becoming an increasingly dangerous threat against forward-deployed troops. Some technological developments have recently emerged to protect friendly troops on the ground from potentially lethal small unmanned aircraft. This section provides some brief examples where adversaries used UAS against friendly or allied forces.
Air Interdiction against UAS Workshops of Armed Groups and Terrorists
During Operation EAST MOSUL, often referred to as the ‘Battle of Mosul’, Iraqi government security forces, and international Operation Inherent Resolve (OIR) forces retook the city of Mosul from the Islamic State of Iraq and the Levant/Dawlah al-Islāmiyah Irāq wa-as Shām (ISIL/DAESH). Over the nine months of warfighting, more than ten ISIL/DAESH workshops producing and modernizing Unmanned Aircraft (UA) were identified. Even under intense pressure, the ISIL/ DAESH continued to develop these technological innovations.

Intelligence revealed that the ISIL/DAESH had a systematic procurement and development strategy for converting commercially available drones into weapons. Additionally, they managed and planned their activities through the establishment of an air operation and observation unit. As a result of the broad possibilities and capabilities offered by UAS technology, the capability portfolio of the ISIL/DAESH increased exponentially in both offensive and defensive operations, thus posing a serious threat to friendly and allied forces as well as the civilian population.4
Furthermore, the other violent armed terrorist organization, the Kurdistan Workers’ Party-PKK has had the chance to capture small-sized armed UA from ISIL/DAESH left over after OIR Raqqa operations and used them in their attacks against the Turkish Armed Forces. In the city centre of Hakkari, an armed (carrying a grenade) small drone used by PKK terrorists to attack a military base was shot down by Turkish Armed Forces in 2016. As some other attacks were examined, C4 type explosive material reinforced with nails was used and carried out in different regions close to Hakkari. It was assessed by Turkish Armed Forces that those small-sized UA were produced as deadly weapons in an isolated workshop close to Syria.5

These small-sized UA can create severe problems for friendly forces on the ground. Their size, small radar and electromagnetic signatures, and quieter operation capability make them difficult to detect and track. This challenge remains the same, and comprehensive threat analyses have been conducted under C-UAS technologies programs. However, these drone workshops are counted as potential AI targets. Identifying the location of the terrorist workshops that produce UA of small size, but with large weapons impacts and their rapid destruction within the scope of AI will allow the friendly ground forces to continue their activities without facing these complex threats on the battlefield. In future Alliance operations against an asymmetric enemy, consideration should be given to attacks against drone workshops like those in the previous examples.
Air Interdiction Against UAS of Peer Adversaries
In contrast to the aforementioned UA workshops of non-state armed groups and terrorist organizations, larger systems offer considerably more attack surfaces for AI operations. Larger armed (detectable and trackable sized) UA are game-changers and force-multipliers on the battlefield. As UA are increasing in physical size and technical capability, the number of inevitable impacts they can create on the battlefield is also increasing. Apart from the UA itself, larger UAS typically include Launch and Recovery Units (LRU), Ground Control Stations (GCS), Communications Equipment, Logistics and Supporting Systems, as well as their respective personnel. These systems are highly critical capabilities for adversary UAS operations. Considering their importance during AI target development phase, these core UAS components might need to be prioritized above other threats. Basically, an interdiction target is one that is worth destroying either during the early suppression period of a battle or by direct engagement of the threats to provide disruptive effects. Accordingly, they need to be defeated well in advance of AI operations to significantly affect the course of adversary operations. Disabling or neutralizing any of the mentioned system components will at least disrupt the associated UAS’ operations.
Targeting Unmanned Aircraft on the Ground: Although UA are predominantly Air Defence targets when airborne, destroying UA on the ground is a viable and arguably better option and well in line with the AI definition of destroying an adversary’s military potential before it can be brought to bear effectively. Like any manned aircraft, larger UA require an airfield infrastructure to host their significant logistical footprint. Intelligence has to provide the basing locations of enemy UAS units, which should be part of the regular Intelligence Preparation of the Operational Environment (IPOE) anyway. However, if strike assets are limited and targets have to be prioritized, focusing on the UAS elements discussed in the subsequent sections may be the more efficient option. It is important to note that even though the destruction of the UA on the ground is a more difficult targeting option, it may be an undeniable AI operational task in terms of its contributions to the overall campaign.
Targeting Launch and Recovery Units: Launch and recovery of UAS are the most critical and demanding phases of the aircraft’s operation. Large fixed-wing UA require an airfield with a paved runway of sufficient length for take-off and landing. Small to medium-sized fixed-wing UA have significantly fewer infrastructure requirements and the LRU is typically more mobile by using a catapult or other vehicle-mounted systems for take-off and landing. Nevertheless, the equipment necessary to launch and recover the UA, as well as its personnel are highly vulnerable during this phase and can be targeted by friendly AI missions.6 Successful destruction of launch and recovery equipment and personnel or the airfield’s runway with anti-runway penetration bombs will cause the UA to remain grounded until the runway is repaired or LRU has been replaced by a redundant system and backup personnel. Notably, it is common practice that multiple UA are purchased with a single set of launch and recovery equipment, so the redundancy of LRUs is likely lower than the availability of backup aircraft, which makes the LRU an even more valuable target. Those UA using runways can be disrupted by an effective AI attack which creates craters on the runway surface. This kind of runway or LRU AI attacks result in indisputable functional and/or possible physical damage to adversary UA during ongoing flights. This target diversity of AI attacks actually has the same effect on the adversary UAS operations.
Targeting Ground Control Stations: The portion of the Control Element, where the aircraft’s pilot and payload operator are physically located, is referred to as the GCS. The physical location of GCS can vary greatly from near the Area of Operations (AOO) to far away and deep inside enemy territory, depending on whether Line of Sight (LOS) or Beyond Line of Sight (BLOS) communications are established. The physical destruction of a GCS will likely disrupt the current operation of all UA linked to it if no redundant system is in place. In the same way as with the LRU, usually multiple UA rely on a single GCS, which makes it a highly valuable target.6 The GCS location will be important in AI target prioritization and AI force allocation.
Targeting Communications Equipment: UA are highly dependent on connection with ground stations for command and control data links. Radio communications between the UA and its remote pilot is a vital component of any UAS. The respective communications equipment for UAS operating in LOS is usually attached to the GCS or can be found near its location. As the mode of operation indicates, radio antennas do in fact require LOS to the UA, hence they have to be placed quite openly and on elevated positions, making them lucrative targets for AI missions. UAS operating in BLOS mode typically utilize large satellite ground terminals with diameters of several metres. These ground installations are usually located at a great distance from the AOO, inside enemy territory or a host nation, so they are less accessible to AI missions. However, the large dimensions of the satellite antennas make them vulnerable to identification by any aerial or space imagery. An array of satellite antennas may indicate a nearby Mission Control Element (MCE) for multiple UA and targeting either the antenna array or the suspected MCE buildings could significantly disrupt enemy UAS operations on a broad scale.6 Depending on the location and type of the GCS, the satellite terminal may vary and the primary satellite equipment which enables the MCE to control the UA’s operation will be far away from the AOO. Home-based UAS control elements may not be identified. Therefore targeting expeditionary enemy personnel, LRU and related logistical supplies at a forward operations base close to AOO might be the best option. Again, it is very difficult to attack and destroy Command and Control (C2) systems linked to such technology. Subsequently, a peer adversary may have a well-developed remotely controlled UAS, and this is especially true with the proliferation of more effective C2 and data link technologies. Even though the destruction of the GCS and C2 systems causes a delay in the mission of the enemy UA, they may recover their effectiveness with the introduction of redundant GCS and link systems. In this respect, AI assets need to strike LRU or UA on the ground before the MCE takes control of UA during remote split operations.
Targeting the Logistics and Support Systems: UAS logistical support refers to UAS lifetime operational support; scheduling issues; delivery of goods and services; maintenance, testing, and fielding of UA; design and operation for reliability, safety, availability, and maintainability; logistics for ground station support and mobile UA platforms; and potentially human operator support. Although a UA does not require a crew on board, it is a kind of flying platform, which requires nearly the same logistics support as most manned aircraft. Thus, UAS logistical support should cover the required support for all subsystems of the UAS including LRU, GCS, MCE, and data link or communications equipment. The UAS logistical support system depends on many different parameters including the type of the UAS, its operational requirements, and its operational environment. For a small hand-launched UAS, relatively little logistical support is required, while larger UAS usually need more logistical support.7 Destroying logistics and support systems of the UAS components is a solid hit on an adversary’s force employment and readiness. It is kind of like cutting off the oxygen that allows UAS military function to operate properly. The destruction of a tactical logistics chain has deep effects and its effects might not be seen in the short-term, but cause inevitable challenges to UAS life cycle management. However, this all depends on where logistical support facilities of UAS are located. Those centres might be embedded into the main airfield’s logistics system, or they may be isolated from the main process. UAS logistics facilities, convoys, or supply chain elements are considered to be in safe areas, targeting logistics and support systems are mainly dependent upon precise intelligence.
It should not be forgotten that these candidate target sets are most likely to be protected by highly integrated air defence systems. The ability to locate and destroy these systems before the AI flight is a big challenge. First, a huge issue is the control of the air in the area of interest. All AI operations are tied to the degree of control of the airspace around the target. Historically, control of air has been a crucial factor in modern air operations’ success, because it prevents enemy actions directly against friendly assets and facilitates the freedom of action and movement of friendly joint forces. Any modest degree of air superiority permits friendly air operations to function without prohibitive interference by the adversary. These operations aiming to destroy UAS components may be used to shape the operational environment or to directly support ongoing military operations by isolating the enemy clearly within the AI target group. Additionally, the effectiveness of AI missions is also dependent upon the joint targeting and tasking cycle fed by timely and precise intelligence regarding the operational environment. This kind of AI operation actually permits AI to be considered as a C-UAS capability of friendly forces. With AI operations, the main actions of AI such as ‘delay the time of arrival of enemy capabilities and the destruction of enemy forces’ will be managed to prevent the peer adversaries’ attacks against friendly forces. Ultimately, successful AI creates a negative psychological effect on the adversary’s morale.
Countering the Counter-Systems: An Excursion
In cases where air operations should utilize UA, air operations planners must research which enemy troops have Air Defence (AD) systems used for C-UAS operations or what type of C-UAS systems they may possess. In terms of the effectiveness of the operations by the armed or unarmed UA, it will be crucial to detect and destroy the enemy C-UAS capabilities embedded inside their AD within the scope of the AI campaign plan. Simultaneously, neutralizing the enemy’s AD systems will also be key to supporting and establishing air superiority over the battlefield. It is nearly impossible to achieve success during the counter-land and air operations without air superiority. After air superiority is gained, all offensive counter operations, including C-UAS operations with AI will be easier for friendly forces. Subsequently, the aforementioned purpose of AI, to delay, disrupt, or destroy enemy forces or supplies en route to the battle area before they can harm friendly forces will be achieved. If the enemy ground force presents a lucrative AD (used for C-UAS operations) target, AI can be conducted to significantly degrade the enemy’s fighting ability. How to achieve a sufficient level of control of the air, which allows for friendly AI operations is, of course, outside the scope of this chapter. The following brief excursion will, therefore, assume that air missions in denied or contested airspace may be primarily tasked to friendly UA in order not to expose manned aircraft to unreasonable risks. In this context, the following section discusses the use of friendly UA against adversary C-UAS systems to enable manned and unmanned AI operations against the target sets discussed earlier in this chapter.
Current Adversary C-UAS Technologies
In late 2017, Syrian non-state militants launched a drone swarm to attack Hmeimim airbase. (cf. Chapter 3, p. 45) In response to the attack, Russia sought to improve its defences against drone systems by working on several models of anti-drone weapons to improve the military’s protection.8 Subsequently, Russia’s Ground Forces were augmented by the introduction of units specially formed to combat enemy UAS. Their primary focus was initially to detect and cause interference against UAS. However, it is planned to eventually equip these units with more direct means to destroy UA. The Russian C-UAS units are equipped with dedicated radars and electronic interference systems to jam the drone’s communications and navigation systems.9
Another system used for C-UAS is the Russian Pantsir-S1, which was originally designed to provide point air defence against aircraft and helicopters and to provide additional protection for AD units against enemy air attacks employing precision munitions, especially at low to extremely low altitudes. These characteristics make the Pantsir-S1 perfectly suited to also counter the complete spectrum from small to tactical UAS and to close the gap between the dedicated C-UAS systems against large-sized UA and drones in the regular air defence units, which are directed against larger medium- and high-altitude long-endurance UA.
A Successful Example of a Tactical UAS versus a C-UAS System
For the first time, Turkey used armed UA as the primary element in Operation Spring Shield (2020) in Idlib. In the mentioned case, Turkey extensively employed armed UA which struck multiple targets in and around north-western Syria, adjacent to Turkey’s southern border. To provide safety for ground troops, these Turkish-made armed UA were hitting and destroying a broad range of military targets from tanks to air defence systems, howitzers, and military bases which demonstrated the efficacy of such devices in a Close Air Support (CAS) role.10

In addition, there was one active Russian-made Pantsir S-1 air defence system deployed inside Idlib for C-UAS. This was a time-sensitive target, posing a real danger to the supporting UA and it needed to be destroyed immediately. The Pantsir S-1 was mounted on its eight-wheel-drive truck sitting placidly as the mini smart ammunition projectile, fired from Bayraktar TB2, proceeded toward it. The Pantsir S-1 active system failed to detect the drone (due to intensive Electronic Warfare operations) and incoming missiles that were flying within range of the radar.11

The above example illustrates how an enemy AD system used as a C-UAS capability was destroyed by friendly UA during part of counter-land attack operations. Without having more AI assets, direct destruction of this C-UAS capability of the non-friendly groups had the desired effects on adversary combat power both physically and psychologically. The destruction of these high pay-off targets was perceived as critical for accomplishing the objectives. NATO might need to evaluate using tactical UA to neutralize adversary C-UAS systems. Some critical takeaways might be transferable to NATO to improve the operational effectiveness of the alliance against peer adversary C-UAS and evolve current abilities to adapt to threats and the changing character of armed conflict.
Conclusion
Any adversary using emerging technologies, like UAS or C-UAS, may have the potential to be a force multiplier that can play a decisive role on the battlefield, and also change the balance of power. Considering how rapidly these technologies are developing, it should be understood that this prediction is an inevitable reality. The military role of both technologies is growing at unprecedented rates. As the capabilities grow for all types of UAS and C-UAS, nations should maintain a focus to ramp up their research and development efforts, leading to further advances and enabling them to fulfil the widest variety of missions. As a result, the battlefield environment has changed, and our adversaries have shifted their capabilities. The evolving security environment and its dynamics will impact the need for the development of future Alliance capabilities. The respective required technologies need to be assessed using innovative ideas to keep our military edge while conducting real-time analysis of NATO current operations.
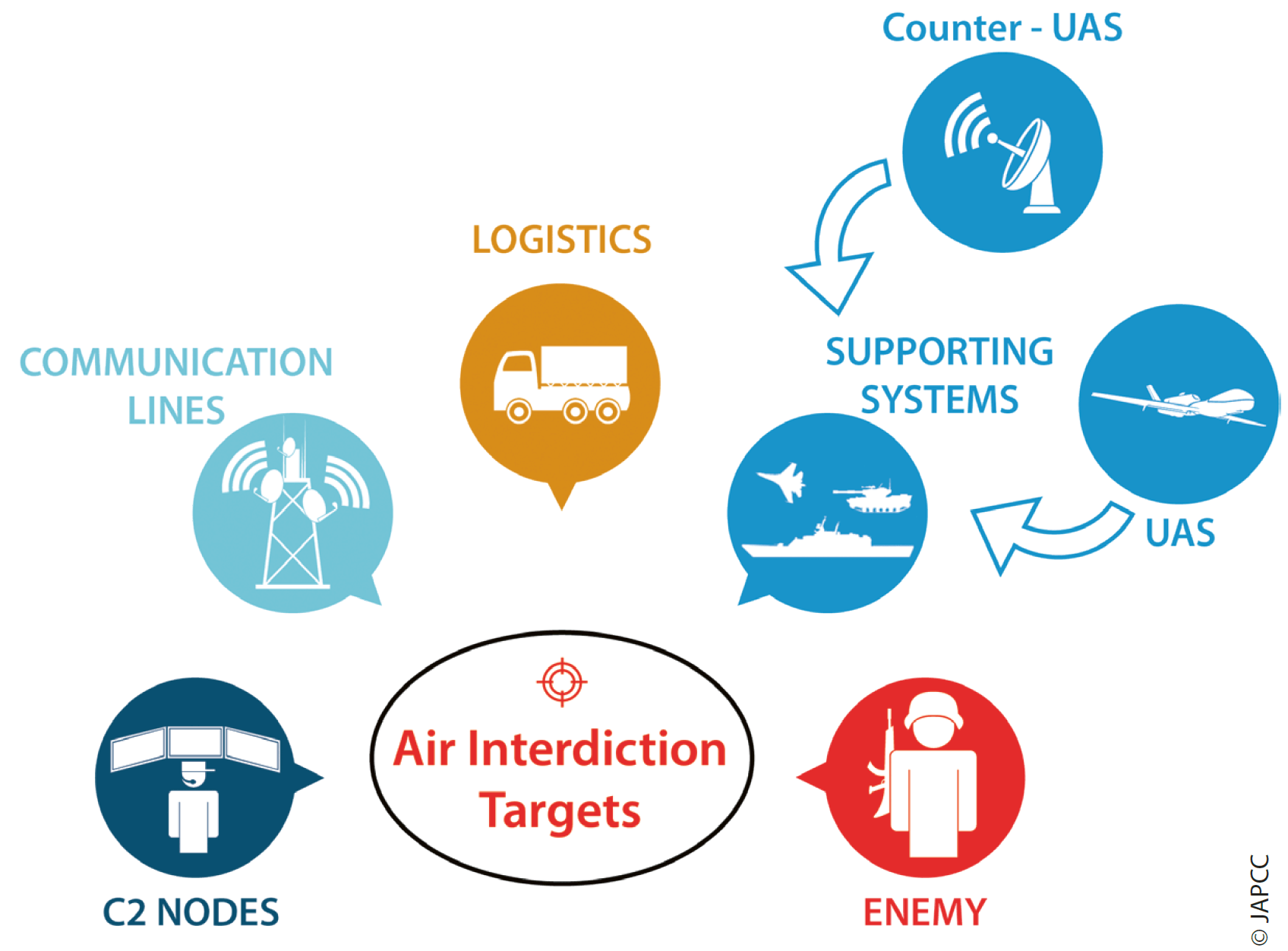
According to those examples depicted above, both UAS and C-UAS are currently a part of adversary capabilities and future perspectives. C-UAS systems which are collocated with existing weapon systems, such as counter-mortar and surveillance platforms, are growing threats to friendly forces on the battlefield and need to be neutralized before friendly forces enter the theatre of operations. The widespread use of all types of UAS by both adversary nations and non-state actors increase the threat intensity level and have potential impacts on friendly battlefield operations. When the adversary systems targeted under AI are reviewed, it is clear that these adversary UAS and C-UAS capabilities should also be evaluated as a new target vulnerability and added to the existing target lists when generating target and threat assessments for AI.
The ability to pinpoint and destroy these systems prior to launch remains a challenge for effective counter-land operations. However, the destruction or partial neutralization of the C-UAS and UAS systems on the ground will lead friendly elements to have both physical and psychological advantages over the enemy. With ongoing and successful AI operations against these new targets, adversary groups will suffer some level of physical and psychological disruption. Sometimes psychological superiority can quickly change the course of the conflict. For instance, attacking and destroying any high-value UA acting as massive surveillance platforms can affect the sensitivities of an adversary’s military morale. Psychologically disruptive effects may prove to be an added benefit to AI objectives. The detailed target risk assessment processes and desired effects should determine the setting of objectives and AI operation flow. We are all dependent on each commander to effectively employ military capabilities to achieve planned AI objectives.












